Short: Achieving the Safety and Security of the End-to-End AV Pipeline
Aug 13, 24
Information
Authors
Noah T. Curran , Minkyoung Cho , Ryan Feng , Liangkai Liu Brian Tang, Pedram Mohajer Ansari, Alkim Domeke, Mert D. Pesé , Kang G. Shin
Conference
1st Cyber Security in Cars Workshop (CSCS) at CCS
Blog
Intro
In the current landscape of autonomous vehicle (AV) safety and security research, there are multiple isolated problems being tackled by the community at large. Due to the lack of common evaluation criteria, several important research questions are at odds with one another. For instance, while much research has been conducted on physical attacks deceiving AV perception systems, there is often inadequate investigations on working defenses and on the downstream effects of safe vehicle control. This paper provides a thorough description of the current state of AV safety and security research. We provide individual sections for the primary research questions that concern this research area, including AV surveillance, sensor system reliability, security of the AV stack, algorithmic robustness, and safe environment interaction. We wrap up the paper with a discussion of the issues that concern the interactions of these separate problems. At the conclusion of each section, we propose future research questions that still lack conclusive answers. This position article will serve as an entry point to novice and veteran researchers seeking to partake in this research domain.
Overview and Research Questions
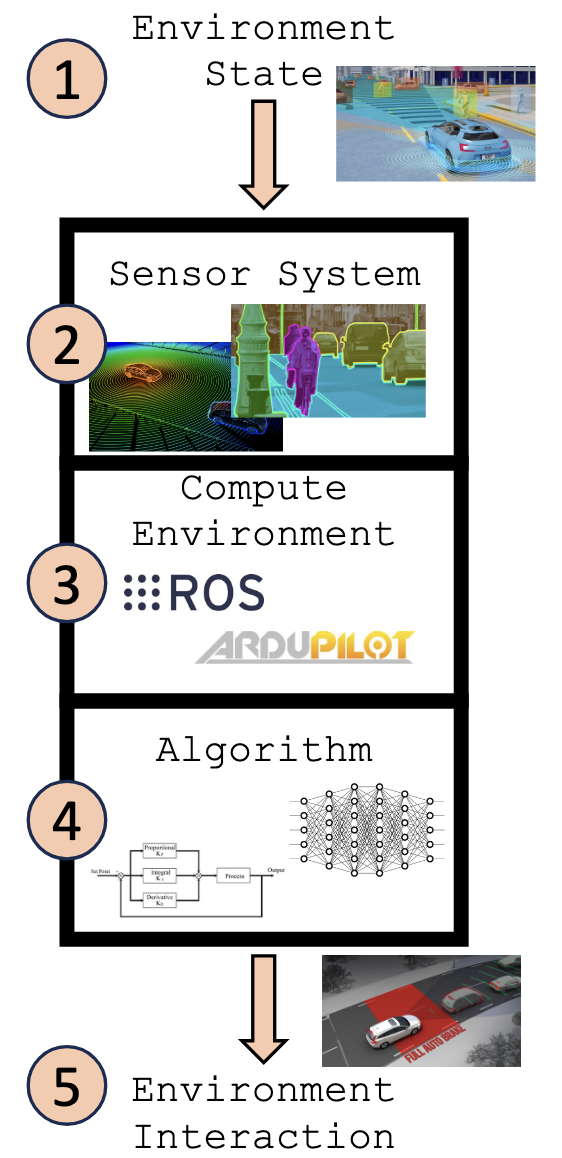
We present a non-traditional overview of the components of the AV. Typically, most introductions to AVs present a Sense-Plan-Act control loop. However, Sense-Plan-Act does not have an abstraction that shows the important portions of the attack surface. In contrast, our representation combines the planning and control of the AV as part of the algorithmic processes, and we expose the middleware as a component between the sensor system and these algorithms.
Research Questions−❶: To what extent do AVs exacerbate surveillance? What are the direct implications of widespread AV adoption, and how will it impact personal freedoms? Can we provide privacy to the environment surrounding an AV without detriment to the AV’s performance (safety and otherwise)?
Research Question−❷: What set of evaluation metrics may satisfy the criteria for demonstrating novel AV perception attacks while simultaneously showing the real impact on the overall AV safety? Likewise, is it possible to find a provably secure defense against sensor attacks that do cause dangerous control outcomes?
Research Question−❸: The complexity of AV software can lead to overlooked vulnerabilities, posing safety risks. Additionally, the emphasis on accuracy often neglects timing and energy efficiency aspects, which are critical for long-term safe AV performance. Can attacks on other attributes such as timing and energy lead to safety-critical failures?
Research Question−❹: How can we reinforce robustness and reliability, both intra-module and inter-module, within our pipeline to ensure preparedness for increasingly complex and unpredictable driving scenarios? Moreover, can such preparation increase defenses against a strong adversary?
Research Question−❺: Future legislation will need to consider how and when AV software can be granted a license to autonomously operate in specific environments. How can this be provided to ensure the public does not involuntarily partake in a dangerous experiment, while simultaneously encourage the further development of AV technology?
Discussion
Recommendation #1: For future research in AV security, a key recommendation is to focus on comprehensive end-to-end testing strategies that encompass the entire system’s operation, from percep tion to control, to ensure robustness and safety in diverse real-world scenarios. This would include the future creation of universal metrics that may be used across all problems to accurately weigh the strengths and weaknesses of various approaches. These metrics may measure various aspects of the pipeline in order to demonstrate where attacks/defenses are most effective, as well as the end result so that one may see the threat that an attack has on functional safety.
Recommendation #2: Effectively utilizing the data from surrounding vehicles and integrating it is essential to gain a more comprehensive understanding of the driving environment. Cooperative perception and planning strategies can significantly enhance safety and security, particularly in scenarios where a vehicle is compromised or its sensors are disrupted. This approach ensures more reliable and accurate sensing outcomes, even in challenging circumstances. Moreover, it’s crucial to consider that drivers themselves can inadvertently be a source of safety and security issues. Even without malicious intent, their unavoidable actions may resemble attack-like behavior to other vehicles in specific traffic situations. Therefore, in addition to the AV technology stacks illustrated in the figure, monitoring and understanding driver behaviors can play a pivotal role in preventing AVs from exacerbating potential hazards.
Recommendation #3: The licenses of AVs should have more concrete and strict regulation for when and how they are provided and enforced. This would include clearer standards for the sort of scenarios that the AVs can provide provable functional safety for. Moreover, these AVs should be required to have well-regulated privacy policies with respect to the data they collect on the road. Packaging privacy requirements with the safety requirements of an AV license would provide an encouraging solution to both issues at once. What remains to be determined is where the regulation “sweet spot" is for strictly enforcing an AV license. Government should seek to avoid deincentivizing the development of AVs, so finding this balance is crucial.
Citation
@inproceedings{curran2024shortavsafety,
author={Curran, Noah T. and Cho, Minkyoung and Feng, Ryan and Liu, Liangkai and Tang, Brian Jay and Ansari, Pedram Mohajer and Domeke, Alkim and Pesé, Mert D. and Shin, Kang G.},
title={Short: Achieving the Safety and Security of the End-to-End AV Pipeline},
booktitle={1st Cyber Security in Cars Workshop (CSCS) at CCS},
url={https://arxiv.org/abs/2409.03899v1},
year={2024},
}"